Data Encryption Made Easy
Data encryption software by CryptoForge™ provides confidence that your information remains yours, even if you were breached.
Our award-winning, easy-to-use data encryption software solution protects your sensitive data for secure storage and while in transit, anywhere it goes.
File Encryption
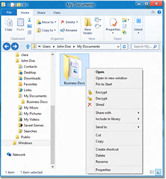
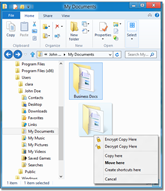
Our software features a file encryption module that allows you to encrypt files and folders of any type and size,
on any kind of media including hard drives, removable drives, USB memory sticks and newtwork folders.
It can encrypt files up to the maximum size supported by the operating system and storage media, for instance up to 16TB on NTFS drives. And
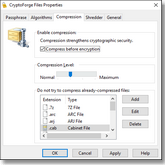
it reduces storage and bandwith costs by combining data encryption with compression, which also strengthens encryption security even more.
Our file encryption solution lets you decrypt files on any computer without CryptoForge installed.
Encrypted Email Solution
Secure email and send encrypted email attachments to anyone you wish. Recipients don't have to install any software to be able to decrypt the secure email attachment.
Our email encryption solution includes a tiny, portable and free app that allows the decryption of files on any computer without
CryptoForge installed. You can freely distribute the Decrypter app along with encrypted files to all your clients, contacts or business partners.
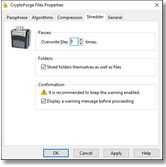
File Shredder
Our data encryption software includes a file shredder, for secure data destruction and disposal, that matches and exceeds DoD specifications (US Department of Defense).
The file shredder can shred files of any size and type, on any kind of drive.
Easy Integration
Our encryption solution allows your organization to easily integrate data encryption software into your existing systems through its extensive command-line interface,
which lets you use all of its power from automated processes and scripts, providing both interactive and server running modes. It even includes a visual tool
to create command-line parameters easily and quickly.
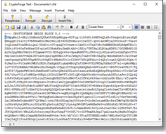
Ciphertext
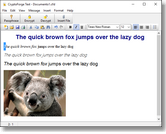
The text encryption module allows you to encrypt text, small files, images, and objects in general, to ciphertext, which you can send by email or any type of messenger app, such as WhatsApp Web or Skype. Ciphertext can even be posted on social networks like Facebook, or sent as Facebook messages. When the software decrypts the ciphertext, it rebuilds any embedded files, images, sound clips, spreadsheets,
or any kind of object the original document had.
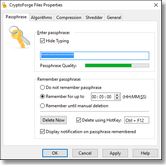
Encryption Features
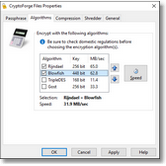
In addition to well-known AES encryption, this data encrytpion software features four strong encryption algorithms: 448-bit
Blowfish, 256-bit AES (Rijndael), 168-bit Triple DES, and 256-bit
Gost. Unique features include multiple encryption (encryption with more than one algorithm simultaneously), file name encryption,
and cipher speed meter.
Free Download
Try CryptoForge data encryption software for free for 30 days for encryption, and then it will work indefinitely for data decryption
(in addition to the free Decrypter app included in the package):

|
Encryption Software...
 CryptoForge Encryption Software CryptoForge Encryption Software
 How to encrypt a file How to encrypt a file
 How to encrypt a folder How to encrypt a folder
 Encryption software reviews Encryption software reviews

Software Screenshots
Click on an image to enlarge.
|
